Archive for the ‘PC’ Category
Description of ‘PC’ Category: PC, short for personal computer. Computers running Microsoft Windows™ operating systems.
Thursday, October 6th, 2011

from http://www.piriform.com/defraggler, October 2011
Defragmentation is a process that mitigates and reverses fragmentation. File system fragmentation occurs when the system is unable to maintain the data in a sequential order. During fragmentation data that is in memory is broken into pieces and dispersed throughout the system. One of the major problems that occur with fragmented data is an increase in the time it takes for the system to access files and programs.
Files on a drive are commonly known as blocks or clusters. These files are stored on a file system and are positioned one next to another. When files are added, removed, or changes the amount of space between these files is altered and the system no longer has enough room to hold the entire file. The system will then fill in these small spaces with portions of new files or files that have been adjusted, causing data to become separated from the rest of the file. This separation creates a delay in Seek Time and Rotational Latency. Seek Time is the time that it takes the head assembly to travel to the portion of the disk where the data will be read or written. The Rotational latency is the delay waiting for the rotation of the disk to bring the required disk sector under the head assembly.
The primary purpose of a defragmentation tool is to sort, organize, and compact similar blocks of data in order to reduce wasted space as well as to speed up access time. Windows operating systems come pre-installed with their own “Disk Defragmenter” utility. This utility is designed to increase access speeds by rearranging files contiguously. Many users feel that the pre-installed defragger isn’t the best on the market and have considered using alternative defragging tools. For the most part defragmentation software all does the same thing but it is very important to only use software from trusted developers. Using a poorly constructed defragmentation tool might cause problems like corrupted data, hard disk damage, and complete data loss. Free software can also lack the necessary support and may not be performing the function that it is meant for correctly.
If you still decide to use an alternative to the one provided with the Window’s OS, the paid options are probably the safest. This is because commercial software like Disk Keeper are put through testing to mitigate the negative impacts. There are also a few free alternatives that are pretty popular like Piriform Defraggler, Ultra Defrag, and Auslogics Disk Defrag.
Before making any decisions you should examine the strengths and weaknesses of free and commercial defragmenting software alternatives. After all, it might not be worth the hassle especially if the Window’s Disk Defragment utility is running adequately.
Have a Great Day!
Dustin
ComputerFitness.com
“> Providing Tech Support for Businesses in Maryland

Tags: data, defragment, defragmentation software, file, files, fragmentation, Software, system
Posted in Desktop - Workstation, PC, PC Maintenance | No Comments »
Friday, September 9th, 2011
It is critical to perform routine maintenance on your PC in order to preserve its performance level. Computers can quickly get bogged down with too much data and the inability to quickly locate your important documents can lead to frustration. The same organizational skills that you practice in the real world should translate over into the virtual space of your computer. Keeping your PC clean and organized will not only help to keep your files easily accessible but it can also reduce your stress and save some time. The following are some simple tips to follow when it comes to organizing your PC files. 
The desktop is the first thing that a user encounters and should be the starting point for cleaning up your computer. Remove the files or programs that you do not use, leaving only the programs that you use frequently. Attach the most frequently used programs to the desktop toolbar. Create labeled folders and group the files or applications appropriately. The typical icon layout will group the desktop icons along the right side of the computer screen however these icons can be grouped and moved elsewhere if beneficial. Based on their level of usage arrange your icons and folders in an order that makes the most sense to you. Additionally you can use desktop wallpaper that displays a grid so you can group and move icons into particular sections or categories.
- Organize your media content:
Keep your music with music, photos with photos, and movies with movies. Typically your computer will have preset folders for your media content, however over time it’s easy for these files to be unintentionally scattered and saved in other locations. You can also create your own media folder which holds separate folders for each type of media content. To provide more organization you can further break down your content, it may require more clicks to access but it will be more specific and easier to locate content. To relocate the files, first sort by media type, select the files, cut, and paste into the new location. (You can also organize these files in programs like the latest version of Windows Media Player)
For Example:
>Media Content Folder
Music
Photos
Video
Or
>Media Content Folder
>Music
>Band Name
>CD Title
>Song Title
>Photos
>Family
>Year
>Event
>Videos
>Genre
>Movie Title
Similar to how we organized the media content, we can also access the documents folder and create more efficient folder architecture. Compartmentalize the various sections of your files, for most it may require folders such as home, work, and school. You can also create more subfolders to further categorize your files. Although folders provide the option to sort your files multiple ways, for a folder that has a lot of files it can be beneficial to further break down the files into file type. (Images, .xls, .Doc, and so on)
For example:
Work \ Company Name \ Project Name \
Work \ Company Name \ Project Name \Word Documents\
Work \ Company Name \ Project Name \Spreadsheets\
Work \ Company Name \ Project Name \Images\
- Organize your Browsing Bookmarks:
If you continue to bookmark web pages without assigning them to specific folders they can begin to blend and become very difficult to find. Folders can be created by accessing the favorites or bookmarking menu on the browser or toolbar that you use. Create new folders and label them according to the areas or subjects that they will contain. Once the folders are created select the appropriate pages and drag them into their new location. During future bookmarking you can designate which folder the bookmark should be stored in.
For Example:
Social Media Sites
Shopping Sites
Email is one of the most common reasons why people use their computers. With the number of emails sent and received every day email organization is often ignored. To clean up your email begin by deleting junk mail and any old messages. Most people keep their mail in their inbox, instead create subfolders and sort your email as you access it daily. If using Microsoft Outlook you can also establish rules for your emails that automatically deliver them to the correct location. Similar to your computer files your email can be separated into categories like social, work, and school. Email folders can also be created to assigned priority.
For Example your email may look something like this:
>Inbox (22)
>School
>Classmates (5)
>Project Conversations with Jack (2)
>Project Conversations with Jill (3)
>Professor (2)
>Assignment Instructions (1)
>Misc. Information (1)
>Shopping (4)
>Purchase Confirmations (2)
>Shipping and Delivery Notices (2)
>Junk (0)
>Trash (0)
These are just a few simple organization tips for your PC. These methods should be done in conjunction with regularly scheduled PC maintenance tasks to provide the best results. These 5 tips along with your own organization methods should help your computer’s performance as well as your own ability to store and quickly sort through data.
Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support to Businesses in Maryland

Tags: computer maintenance, Email, files, folders, increase productivity, Maintenance, media content, Organization, pc
Posted in Desktop - Workstation, Email, PC Maintenance, Storage | No Comments »
Friday, September 2nd, 2011
In our past blog postings we have talked about computer maintenance issues like performing backups, removing unwanted files or programs, and increasing the speed of your computer. In our posts for helpful hints to extending the life of your computer we have also briefly mentioned external conditions that can impact your computer but we have yet to address how to clean the actual PC and its peripheral components.
Keeping your computer and work environment clean is critical to the operations of your system and it can drastically extend the life of your PC. Dust is a common cause of overheating and the deterioration of important computer components. Computers may have advanced significantly but dust and dirt can still present major issues and glitches for internal elements. It is estimated that up to 70% of computer hardware problems can be attributed to dust and improper maintenance. Computers and external equipment should be cleaned routinely in order to prevent unnecessary problems caused by dust.
Although the fans of a computer are vital for the ventilation and cooling of the system they also provide a perfect opening for dust. Along with the cooling fans any small openings on monitors, keyboards, or any other devices are also dust gateways. In short the dust can settle on internal components and prevent the release of heat, causing the computer to short and overheat.
When everyday household items aren’t enough there are many products to choose from that are designed specifically for PC maintenance. Some of the available products include microfiber cleaning clothes, CD/DVD lens cleaners, anti-static monitor wipes, LCD cleaning solutions, aerosol duster, anti-static dust vacuums, wet wipes, and screen protectors.
Basic tips that you should know before cleaning:
- Clean the area surrounding the computer before cleaning.
- Always spray the cleaning solutions on a rag first, never apply directly to the computer or monitor.
- When using compressed air, always hold the can up right.
- Do not touch any internal CPU component without wearing an anti-static wrist band or using an anti-static mat.
- Never use a regular vacuum to capture the dust (only use an anti-static computer vacuum).
- Do not attempt to clean the inside of a computer monitor.
- Wait to clean the monitor until it is unplugged and cooled down.
- Unplug the computer before cleaning.
- Do not touch an LCD screen with your fingers and do not use any unapproved liquid to clean your LCD screen.
The Keyboard:
- Disconnect the keyboard from the computer and reconnect after completing the following.
- Hold the keyboard vertically while blowing the keys off with a can of air duster.
- Use anti-bacterial wipes to wipe the surfaces of the keyboard.
- Dampen a Q-tip with rubbing alcohol to clean in between keys.
- Wipe down USB cord with an anti-bacterial wipes.
The Mouse:
- Disconnect the mouse from the computer and reconnect after completing the following.
- With an optical or laser mouse you can use a lint free cloth to clean the bottom lens area.
- You can also use compressed air or a dry Q-Tip to remove the dust from the cracks.
- Use an antibacterial wipe to clean the top portion and the USB cable.
- If you still use an older trackball mouse follow the previous steps in addition to removing the bottom plate and wiping the computer mouse ball with a lint-free cloth dampened with isopropyl alcohol. Use a Q-tip to clean the inside of the mouse where the mouse ball sits.
The Monitor:
- Make sure the monitor is turned off and cooled down (Don’t turn it back on until dry)
- When cleaning an older CRT monitor it is ok to use a regular glass cleaner like Windex just as long as it is applied to a rag and not directly on the monitor.
- For LCD screens avoid using a cleaner, use either a soft cloth that is dry or lightly dampened with plain water. (Products like KlearScreen can also be used)
- Use lint free or a lightly dampened cloth to wipe other surfaces and vents.
- You can also use a can of compressed air or an anti-static vacuum to remove dust from the grooves and vents.
- Don’t forget to wipe the monitor’s cable and power cords.
The CPU Tower and Fans:
- Shut down the CPU and remove the power cord from the wall outlet.
- Remove the power cord and attachment cables.
- Place your computer tower on a stable platform.
- Use antibacterial wipes to clean the outside shell.
- Open the CPU Case. (May need to use a screwdriver)
- While wearing an antistatic wrist strap that is attached to the metal frame of the CPU tower begin using the compressed air to expel the dust from the case.
- Try to blow indirectly or gently on the motherboard and slots so not to damage them.
- Use the compressed air to remove the dust from the power supply and CPU vent.
- Replace the CPU case and wipe down the power cord.
The Disk Drives:
- While the CD/DVD tray is open use compressed air to gently clean out the dust. Avoid using too high of a pressure for it may cause damage to internal components.
- Use a CD/DVD Laser Lens Cleaner to remove the dust from the player’s lens.
CD’s and DVD’s:
- Use a CD/DVD cleaning kit or you can use a clean soft cotton shirt or rag to remove dust.
- Always wipe from middle to edge and never in a circular motion.
- To remove a substance you can use water as well as rubbing alcohol.
USB Connectors and Ports
- Use compressed air to gently clean USB ports as well as the USB plugs on your peripheral devices.
Battery Contacts
- Purchase a battery contact cleaner or clean the contact by rubbing them gently with a cotton swab that has been slightly dampened with alcohol. (Avoid applying too much pressure)
These simple tasks should be performed on a routine basis to get the maximum results and prolong the life of your computer. If cleaning of these components is neglected then the dust and dirt will eventually choke out the performance of your machine. Hope these tips will be helpful with keeping your equipment clean.
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: cleaning, computer, computer maitenance, computer tips, CPU, Peripherals
Posted in PC Maintenance | 1 Comment »
Friday, May 6th, 2011
As helpful as technology may be to businesses it can also present certain challenges. If poorly managed, business technology can often prove to be just as harmful as it is beneficial. This is why we have IT professionals or IT departments. Regardless of how much equipment a company may have the role of an IT department is a full time job especially when you consider the possible strain most companies place on their technology and their need to prevent any malfunctions.

Whether it is a single computer and printer or ten networked computers running off of a server it is mostly the IT department that handles the purchasing, installation, updating, management, and repair of company technology. In order for an IT department to be successful and maintain the integrity of the technology it should possess the following characteristics.
- Qualified and motivated staff
- Appropriate IT resources
- Effective department management
- Proper IT procedures
- Regular meeting, documentation, and review
It is the goal of an IT department to not only fix and manage the company equipment but to also ensure the security of information. To do so an IT department should be performing routine tasks, that includes establishing policies and procedures, updating equipment, and running diagnostics. The majority of work done by these departments should be preventive measures so that when problems do arise they already have procedures in place that detail immediate solutions. Now of course most IT departments cannot predict every incident that has the can occur however they should come pretty close to being able to recognize the most frequent or detrimental threats. Various simple but overlooked tips for a company and IT departments include,
- Password Policies, many users choose to utilize a password that is easy to remember rather than one that is sufficient to protect critical information. A company or IT department should implement a password policy that details and enforces the use of Strong passwords.
- Remote Access Policies, because many company employees need to be able to access company information from home or when traveling, a proper remote access policy should be drafted according to the specifications set by the IT department.
- Appropriate Use Policies, detail what resources should be used and how to use them appropriately. Having an acceptable use policy, whether it is for the use of the equipment, email, or the Internet can potentially prevent equipment errors and system vulnerabilities.
- Scheduled Backups, performing regular backup’s archives important information. In the event something does happen and wipes out your information you will still have the latest archived data to restore.
- Scheduled Updates, establishing automatic updates or routinely checking for software updates manually keeps software like anti-virus, anti-spyware, and firewall protection working properly and aware of the latest security threats.
- Routine System Checks, by running diagnostic tests you can see how your system is performing, document, and perform any necessary adjustments.
- Equipment Checks, similar to routine system checks this entails testing the equipment and making sure it is performing properly.
- Proper Training, to prevent the misuse of equipment all employees should be trained and well informed of the appropriate and inappropriate uses.
- Think Proactive, one the biggest errors when is comes to IT is waiting till something happens. It is most important that you don’t wait till it is too late to create the policies, implement the procedures and protect your technology.
It is extremely important that these bare minimum IT requirements be utilized in order to protect your business’s information and equipment. Even if your company does not have an IT department, you yourself should be implementing some of these suggestions or hiring an IT professional to assist you in protecting your technology. Don’t wait until an IT disaster strikes before you take the appropriate actions.
Is your IT department doing their job? What do you think is the most important element for managing your IT?
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: computer, equipment, Information Technology, IT, IT department, Maintenance, small business, technology
Posted in Information Security, PC Maintenance | No Comments »
Friday, February 4th, 2011
 No one likes to spend more money when it can be avoided. Instead of replacing a computer we can try to extend the life of our current one. There are several simple tasks that we all can do to keep our computers going strong for as long as they can. Of course technology will continue to advance and there will always be faster processors and larger storage drives just around the bend, but in most cases the computers that we use now are more than adequate. If properly maintained our computers will be able to last a long time and prevent unnecessary spending on computer equipment in the future. No one likes to spend more money when it can be avoided. Instead of replacing a computer we can try to extend the life of our current one. There are several simple tasks that we all can do to keep our computers going strong for as long as they can. Of course technology will continue to advance and there will always be faster processors and larger storage drives just around the bend, but in most cases the computers that we use now are more than adequate. If properly maintained our computers will be able to last a long time and prevent unnecessary spending on computer equipment in the future.
There are two primary aspects of computer maintenance that I would like to look at, the computer’s external and internal environments. The external element takes into account physical factors such as the environment, treatment, and storage of the device. On the other hand the internal aspects involve system maintenance, security software, and software updates.
When attempting to prolong the years of a computer it is easiest to start with the physical facet of computer maintenance. After all what good is taking steps to protect the information on the system if we are not going to care for the actual equipment? Just like most things in life, a computer in good physical condition takes effort and the right environment. The most important environmental factors that can affect the life of a computer is temperature, humidity, electricity, an air quality. Below is a list of helpful tips on what you can do to extend the life of your computers regarding both internal and external components.
A computer should be stored in 60-85 degrees Fahrenheit, any extreme temperatures can damage internal components.
Minimize static electricity by keeping humidity levels at about 50%.
Keep air circulating through your computer by making sure any vents on the computer are around 4 to 5 inches from any obstructions. Use air filters or ionizers to avoid dust build up and cleaning the computer and any vents frequently.
Use surge protectors or an Uninterruptable Power Supply (UBS). Common electrical problems such as surges, blackouts, brownouts, spikes and sags can cause damage to your computer.
Avoid eating or drinking over the computer- Even though spills are easy enough to clean up problems can surface when liquids accidently get into the system. Liquids or any foreign elements introduced into a computer mainframe can cause irreversible damage. Additionally this is also a major problem for peripheral input devices like a computer mouse or keyboard.
For more physical maintenance suggestions visit Computer Environment Maintenance!
Once the physical setup of the computer is maintained properly you are that much closer to ensuring a long life for your computer. It becomes equally important to take care of the hard drive and other internal features of a computer as well. The following are suggestions to keep your computer healthy.
- Perform important software updates by establishing automatic updates.
- Utilize security software like anti-virus, anti-spyware, and firewall protection.
- Add more disk space, if necessary.
- Perform weekly and monthly maintenance. This includes clearing away old files, performing disk drive clean ups, managing your startup files, defragmenting your disk drive, and clearing temporary internet files.
The overall life of your computer relies on the management of both its physical and internal features, so be kind to your computer and it could be kind to your wallet.
Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: computer, extend, extending computer life, helpful, internal, life, physical, virtual
Posted in PC, PC Maintenance | No Comments »
Wednesday, January 5th, 2011
 For most of us we use computers because they make mundane tasks easier and we typically don’t think twice or concerned about how they are able to accomplish all that they do. Have you ever wondered what makes your computer tick? It would be helpful to be aware of the basic components that make up your computer. Whether it is to understand a sales person, identify a problem, or for a general understanding, knowing the basics about your computer can be very useful. For most of us we use computers because they make mundane tasks easier and we typically don’t think twice or concerned about how they are able to accomplish all that they do. Have you ever wondered what makes your computer tick? It would be helpful to be aware of the basic components that make up your computer. Whether it is to understand a sales person, identify a problem, or for a general understanding, knowing the basics about your computer can be very useful.
You probably know that your computer is made up of both hardware and software. Software is the programming that tells the computer what to do, how to do it, and which devices to use. The following are hardware devices located in your computer.
#1 – CPU
A CPU or Central Processing Unit is the processor or brain of your computer. This small device is the most important component of your computer. It understands the programs, receives instructions from the user, and delivers the results.
#2 – RAM
Random Access Memory or Computer Memory enables space for the computer to read and write temporary data. The data that is stored in the RAM is only available to the CPU while the computer is running and once the computer is turned off the data being stored in RAM will be cleared.
#3 – Hard Drive
The hard drive is the storage center of your computer. It keeps the contents of your desktop and is accessed by RAM. The RAM displays the information while the hard drive stores it.
#4 – Video Card and Sound Card
These cards have their own RAM and although it is this RAM that holds the data you need to hear or see, it is the video and sound card that transfers it into actual images or sounds. A video card transfers the data to the monitor whereas the sound card transfers the data to the speakers or headphones.
#5 – Network Interface Card (NIC)
A NIC is used to pass on information from your PC to a broadband modem. It both sends and receives data over a local area network (LAN).
#6 – Mother Board
A Mother Board is the largest component of a computer is a circuit board that holds or connects to all of the other components.
#7- Computer Software
Computer Software is any program that has written instructions or machine code that is to be carried out by the computers components. Software basically tells the hardware what to do and how to do it.
Additional components include input and output devices. Input devices are used to communicate messages or instructions from the user to the computer and output devices transmit the results from the computer to the user.
| Input |
Output |
| Microphone
Keyboard
Mouse
Joystick
Scanner
Webcam
Digital Camera
Touch pad
Touch screen |
Speaker
Monitor
Printer
Headphone |
It’s clear that you don’t necessarily need to know what makes up your computer or how it gets things done. But it is still always good to have some understanding of what is going on behind the scenes.
For more information on computer components check out the following links:
Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support to Businesses in Maryland

Tags: component, components, computer, computer devices, hard drive, Software
Posted in Hardware Overview, PC, PC Maintenance, Software | 1 Comment »
Friday, December 31st, 2010
 Hello everyone, this is Dustin and I am back to help you with recapturing your computers speed. Hello everyone, this is Dustin and I am back to help you with recapturing your computers speed.
Have you experienced a decline in your computers speed or are you un-happy with the speed of your system? At some time or another we all have endured a slow startup, encountered simple tasks that have taken way too long, or suffered with speeds less than what we have come expect from our machines. In an attempt to salvage the fast processing speed that you may once possessed here are some simple methods that will help you regain and maintain speeds that you can appreciate.
- Check your security software- Run antivirus, and anti spyware scans!
- Using programs like McAfee Protection Software or Norton Security programs can identify and eliminate threats that can cause your equipment to run slower. These threats can infect your system causing harmful damage to your data and take up precious resources on your hard drive.
- Manage your startup folder- Eliminate the programs that are not needed!
- The start up folder contains files of any programs that you or software manufacturers have designated to start up automatically when your computer is first initializing. They can often drain the performance of your computer and this folder should only include the programs that you will be using immediately or those important to your computers operations.
- In order to fine-tune the startup folder you will need to access the system configuration folder. This can be done by expanding the Start menu, Clicking Run and then typing MSCONFIG. (Windows 7 uses the Search application instead of RUN.) Once the Configuration window appears click the Startup tab and carefully select the programs that you are positive that you do not need for startup. Save and exit, restarting your computer is required for any setting to take effect.
- Additionally you can also manage their startup programs with the security software previously mentioned.
- Clean up your hard drive- Remove the applications you no longer!
- If your hard drive space is currently occupied by programs that you don’t want or will never use again it’s advised that you clear them off your system. Be sure that these are un-needed programs. Any programs that you are unsure about leave in place, for removing certain programs could cause more problems.
- To edit your programs enter the Control Panel, open the Add or Remove Programs function (Windows Vista and 7 “Programs and Features”). When the list of program populates select any program that you wish to amend. You can even sort by the last used date or installed date. Follow the uninstall procedures for each individual program and restart your computer if necessary.
- Trash any useless files
- Delete any redundant or unwanted photos, music, movie, or document files that you are no longer need.
- Most of the time this can be done by simply locating the file that you wish to eliminate and dragging it into the trash can. You can also right click and select delete as well as highlighting it and pressing the delete key.
- In order for it to be permanently deleted, access or right click the Recycle Bin and execute the permanent delete option.
- Buy more space- Get an external hard drive!
- External Hard Drives are available and come equipped with various sizes.If your files are important and you would like to keep them rather than deleting them, this is your best bet. Storing surplus files on an external drive provides more space and still allows for easy access.
- Other Computer Data Storage include: CDs, DVDs, Flash Drives, and smart cards. Online storage centers like iBackup are also available.
- Clear away Temporary Internet Files!
- In the “My Computer” window, right click on your hard drive (C:), right click Properties (General Tab), you’ll see a link for Disk Cleanup. After a new window opens, you’ll see an option to delete Temporary Files, check the box, then click Clean up. This is a good way to clean up any data left over from installations or web browsing that you won’t need anymore.
- Perform a disk clean up!
- The Disk Clean up process will search out any unused or unnecessary files or folders on your PC that are safe to delete.
- To perform a disk cleanup access the Start menu, locate the accessories menu in the programs folder, scroll down to system tools and select disk clean up. Or enter cleanmgr in the Run application box located on the Start menu.
- Execute a Disk defragment.
- Disk Defragmentation searches out similar files on your hard drive in order to consolidate or group the similar files or applications together. Files can often become fragmented and cause a computer to run slower because it has to search harder to locate them.
- The Disk Defragmentation program can be found on the same menu as the disk clean up program described in the previous method.
Additional Tips to help increase your computers speed:
- Keep windows up-to-date using Windows Automatic Update.
- Add additional RAM
- Maintain above 15% of free space on your hard drive, again an external hard drive can assist with any overages.
- Obtain Registry Scan software
Hopefully by using some of these techniques you will be able to see and enjoy an increase in your computers speed.
Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support to Businesses in Maryland

Tags: computer, computer running slower, computer speed, hard drive, program
Posted in Desktop - Workstation, PC Maintenance | 1 Comment »
Friday, December 17th, 2010
 10 Tips to Help Keep Your Data Protected 10 Tips to Help Keep Your Data Protected
Hey everyone I’m Dustin, welcome back to our blog.
Worried about your information going out across the World Wide Web, continue reading to learn how you can get protected against loss of data, data theft, and data corruption.
- Physical Protection: Passwords, firewalls, and virus scanning are great but please don’t forget the basics. Keep your computer physically locked up or only leave it where you know for a fact that it will be safe. Even people you know can access your computer and bring unwanted problems if you give them the chance. Devices like security cables and alarms can be used but are not full proof. Making a note of the computer’s serial number can also be helpful if a theft does occur and needs to be reported. (Computer Protection Devices)
- Don’t be naïve not everyone is nice: Don’t give out your personal information to people you don’t know, it’s not a normal for strangers to ask for your address or birthday when you first meet them. Don’t provide too much information to social networking sites.
- Use Antivirus and Spyware programs: Using good Antivirus software is not enough anymore. New malicious programs are created and discovered every day so it is important that you not only have Antivirus software but that you keep it up to date as well. Antivirus programs scan, track, and remove any problems from your hard drive. Like Antivirus software a spyware program can detect and eliminate any spyware that has made a home on your hard drive. Many Antivirus programs do have anti-Spyware included, if yours does not, you will need to install a separate program for Spyware. Spyware can often track your web usage, violate your privacy, add unwanted features, and take up your computer usage for its own purpose. (Learn More)
- Back up your information: If you don’t already have a back up of your hard drive you should create one. Sooner or later you may encounter a problem that requires a complete hard drive wipe so avoid the hassle of re-building your information and create a backup. There are many programs that will automatically create a back up for you some of them programs include Symantec Backup Exec, Ace Backup, Nero Back it up, Save Me PC, and Evault. Chances are that if you have a security or antivirus program on your computer they will establish a hard drive back up already on a routine basis.
- Activate your Firewall: To make certain that your firewall (in Windows) is active access the control panel, go to network and connections, and select firewall settings. Additional programs like Norton Security Suite and McAfee Security provide additional firewall settings. A firewall acts as a barrier between the internet and your computer protecting it from outside access and intrusive problems. Firewalls are essential to controlling the traffic through the various network ports.
- Learn and Beware: Educate yourself, don’t be fooled, and take a closer look to see what information is accurate and safe. Avoid pop-ups asking you to install software, only install free software that you are sure about and no is safe. Don’t open attachments without scanning first and don’t open links in your emails that you suspect might be bogus.
- Avoid Phishing: Phishing is when emails falsely claim to be an existing organization that you do business with. These emails redirect a user to a website created to look like the legitimate site and then users are asked to update their personal information. Mean while the real company has no need of asking for updated information and you just supplied it all to a criminal. Be cautious of emails expressing urgency and avoid links and submission forms asking for financial information. Sensitive information like this should only be communicated using a secure webpage. (More about protecting yourself against phishing!)
- Make sure pages are secure: Whether it is to purchase items, check bank accounts, or to logon to other sensitive information be certain that site is displaying a security icon on the browser window. In addition to the locked icon, an encrypted web site URL will include https instead of the unencrypted http. Depending on the web browser that you are using the icon will be located in various locations. Take the time to familiarize yourself, knowing where yours is located could prove to be very beneficial. If using Internet Explorer the icon is located next to the search dialogue box at the top right and in Mozilla Firefox it is located in the lower left hand page border. Clicking this icon will launch a separate window detailing the security properties of the webpage. (How to tell if the Page is Secure)
- Create strong passwords: A password should be easy for you to remember and hard for others to figure out. A strong password should be 10 to 14 characters in length. The longer the better but only if you’re able to remember it. Avoid any password based on repetition, dictionary words, letter or number sequences, usernames, relative or pet names, romantic links (current or past), or biographical information (e.g., dates, ID numbers, ancestors names or dates). A password should include numbers, and symbols if allowed by the system. If the system recognizes case, use both capital and lower-case letters. On another note about passwords don’t leave them out where people can see them. A strong password is nothing if you leave a hard copy of it under the keyboard, taped to the desk, or even worst attached to the monitor. Hard copies should be kept in a digital wallet or safe. Also switch it up don’t use the same password for everything. If someone can get into your email that is bad enough you don’t want to give them access to your bank information also. An addition authentication tip is to confirm your user account does not have administrative access on your computer. If for example you are a regular user and despite having anti-Malware software installed, some malicious software gets through, the malware software would only be able to affect your profile and not your computer’s operating system as regular users cannot install most software. (How to Create and Strong Password)
- Wi-Fi Settings: When using public or personal Wi-Fi, be sure to turn off file sharing (Windows) by going to your control panel, selecting network and connection, tab to advanced settings and adjust accordingly. In addition you can activate privacy settings and change the firewall configurations in the same location. Make sure that you have an active firewall and ensure that you turn off the Wi-Fi when no longer using it. It’s also worth mentioning that users should always have their home Wi-Fi connections encrypted so users can’t stand around your house and access it. Also make sure no one is hovering to get your login password.
Hope these tips can help! It is only by taking preventative measures like these that we are able to hopefully stay ahead of cyber crime.
Keep your information Safe and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support to Businesses in Maryland

Tags: Firewall, Information Security, Software, strong password
Posted in Information Security, Mac and PC, PC, PC Maintenance | No Comments »
Friday, December 10th, 2010
Hey everyone! Dustin here, welcome to our blog.
Many of us have already seen the Windows 7 advertisements but have continued to utilize previous operating systems. Are you still holding out on the windows 7 upgrade?
Here are 5 reasons why you should not wait any longer. Updating your operating system is crucial for both the security as well as usability features.
Occasionally an operating system may appear to take a few steps in the wrong direction but Win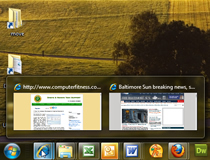 dows 7 is certainly not one of them. As operating systems continue to advance the latest versions are able to add features, especially those learned from previous versions short comings. The following key features generate both increased security as well as usability for users. As operating systems go Windows 7 is Fantastic! dows 7 is certainly not one of them. As operating systems continue to advance the latest versions are able to add features, especially those learned from previous versions short comings. The following key features generate both increased security as well as usability for users. As operating systems go Windows 7 is Fantastic!
1) The Smart Design
The Windows 7 task bar immediately catches the user’s attention. The new task bar has a better looking design than previous versions and its functionality is also unmatched.
The Windows 7 Live Task Bar Preview allows users to catch a glance at their open applications without having the window selected. Hovering over an icon in the task bar creates a window that shows what is going on in each open application. Preview may be the wrong name since within these windows users can now play, pause, or close the applications. In previous OS versions the preview window was strictly a quick snapshot, but with Windows 7 those days are long gone.
Rearrange your taskbar, this time around the tabs located on the task bar can be organized and relocated in an order that is more desirable to the individual users. Rather than opening and closing applications in the order you want them to appear in the task bar they can now easily be rearranged by simply dragging the icons. The task bar now permits users to pin selected programs for more convenient use. Windows 7 remembers user activity and will now store most frequent programs. The logs of recent programs are referred to as jump list. Right-clicking on a program in the task bar opens a jump list where users can navigate recent and popular applications.
Establishing Jump List and Pinning programs to the task bar build upon the Windows 7 experience. All of these features and designs fully harness the ease and power of the Windows 7 Task Bar.
2) The Efficient Performance
Windows 7 is now even more efficient and responsive. On top of its improved task bar working with multiple windows is now even easier.
Snapping snaps the open windows into a position that is selected by the user. A user can drag the window to the preferred location and adjust the size accordingly. The snapping feature creates a desktop in which applications can be open simultaneously side by side. Along with the Snap element the Windows 7 OS now reacts even faster to user instructions. It starts up and reawakens from sleep mode efficiently, connects to wireless networks quicker, recognizes external devices and locates files faster than ever.
The Response Time is much better than previous versions and your computer will now be waiting for you as opposed to you having to wait for it.
Also helpful is the Search Entry Feature which is not completely new but has been expanded to search even more file types and locations. Pretty much if you’re having problems locating something on your computer its only a click away with the Windows 7 Search tool, Search everywhere and everything! This OS has been reconfigured to operate using less memory. While using less memory your PC’s speed and performance is greatly enhanced.
3) The Enhanced Security
It is always important to have an up to date operating systems. The older your OS is the more likely there are holes or faults that make you and your information vulnerable. Window 7 is new so any defects have yet to be discovered or exploited.
On the Ultimate and Enterprise editions BitLocker Drive Encryption is also available. BitLocker allows users to set up their hard drive to be completely encrypted leaving every document and file locked for security. Windows 7 has greatly improved the system backup/restore settings as well as their accessibility.
The Action Center found in the control panel is where settings about firewall, antivirus, and updates are found. The Action Center ensures that the most recent updates are installed and functioning properly. Microsoft Security Essentials is a free download available to Windows 7 users and actively protects against viruses, worms, spyware, Trojans, and malware. The Windows Defender Software also helps against slow performance, pop-up ads, and spyware among other threats.
The Windows 7 Parental Control Features have also been enhanced and are easier to use than those found in Vista. The multitude of security features that this OS offers makes users feel extremely secure and is a must for any PC.
4) The Astounding Entertainment
With Remote Media Streaming Windows 7 users are able to view their home PC’s media library while away. After a quick and simple set up your home media library will be available over the internet without copying the original files.
With the password protected Home Group feature, linking computers and devices is a quick set up away. By home grouping media it can be sent to other computers running Windows 7 using the Play To element. Users who also have an Xbox360 can send media to their televisions. Applications like the improved Windows Media Player, Roxio, Enhanced DVD Maker, and Internet TV only add to the Windows 7 enjoyment.
5) The Fun Personalization
Windows 7 comes with a host of new Wallpapers, Desktop Icon and Window Themes. Users can select the theme that works best with their style and customize their desktop to their comfort level. The return of Gadgets also increases the amount of personalization ability a user has. Gadgets are small applications that are often quick references, games, or pictures. With the release of Windows 7 now even more gadgets are available and have been improved for the OS.
Other mentionable features that are pretty cool include Shake and Peek. Clicking and dragging an application rapidly back and forth drops the other open windows making the one you shake easy to see. And Peek allows users to see past the open windows and select the one you want. Windows 7 customization ability now makes it an even more pleasure to operate.
In conclusion I would say that it is definitely apparent that a lot of thought and time went into creating Windows 7. Whether your reason to upgrade is to enhance security, enjoy the awesome usability, or to experience the cool design, The Windows 7 Operating System is worth the upgrade or full purchase price. Just in case you’re still not convinced here is more information on the Windows 7 OS (compare Windows 7 editions)!
Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support To Businesses in Maryland

Tags: Operating Systems, task bar, Windows, Windows 7
Posted in Desktop - Workstation, Operating Systems, PC, Software, Windows | 1 Comment »
Tuesday, November 23rd, 2010
 Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums. Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums.
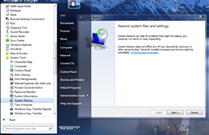
Sometimes bad things happen to your PC. It happens to the best of us. Something goes wrong and before you know it, it’s time to break out the dusty restore discs. Well, there are ways around having to burn your system to the ground. One of these ways, built into the Windows operating system, is the Restore Point software.
Restore Point sets up places in your system where you can revert back to in case of errors. This feature is great for several reasons. First of all, you can choose when to set these. By doing this, you can schedule them or just have them automatically occur when you’re installing new programs. This is good in case the program or update does damage to your machine’s stability. You simply roll back to the start date and you’re good to go.
Another beneficial aspect of Restore Points is that they are usually safe in the case of a Windows failure. This is not to say that if your HDD breaks down, you can just use a Restore Point. Rather, you can sometimes use them in conjunction with a system restore disc or copy of Windows to get back to where you were from an OS standpoint.
Now, the points are not to be confused with complete system backups. You’ll need either third-party software or Windows 7 Ultimate to do that. However, the Restore Points do allow for users to revert to previous versions of the Registry and various Windows aspects.
More Info
Microsoft Windows System Restore
What is Windows System Restore?
What are the system recovery options in Windows 7?
-Josh
ComputerFitness

Tags: pc, Recovery, Safety, System Restore, Windows, Windows 7
Posted in PC | No Comments »
|













 Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums.
Hey, everyone, Josh from Computer Fitness back with another award-winning article to help you with your computer conundrums.

