The security of your business’s website should be one of your highest priorities. A secure website is one of the best ways that you can establish trust with your customers. The security of your website will directly impact your number of visitors and has the potential to hinder or boost your sales. With the massive number of website intrusions this year alone, hacking has become a major concern for most online shoppers. Whether it is to protect your website or your customers personal or financial data, a secure website is a must have. The following are some tips for creating a strong and secure website environment for your consumers. 
Use a Strong Administrative and Database Password:
Creating a strong administrative and database password will prevent hackers from accessing the admin interface and from taking over your entire online business. If a hacker does gain entry to your website’s administration panel they can pretty much do whatever they please from defacing your website to committing fraud by pretending to be you or your company. To learn more about creating strong passwords visit Elements of a Strong Password.
Secure Admin Email Address
An admin email address is used to login to your web server, CMS, database. It should be kept private and different from the one that you have on your contact page.
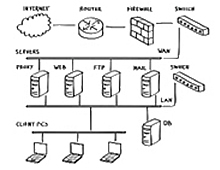
Make sure you have Firewalls Implemented:
Configuring a firewall will help prevent unauthorized access to your site and acts as a filter for the information that is sent to and from your website. You should configure your firewall to the highest security preferences so that it will deter hackers from attempting to gain entry to your site.
Update Your Antivirus Program Regularly:
New malicious programs are created and discovered every day so it is important that you not only have Antivirus software but that you also keep it up to date. Antivirus programs scan, track, and remove any problems from your hard drive. Like Antivirus software a spyware program can detect and eliminate any spyware that has made a home on your hard drive.
Read the Latest Information on Tech Blogs:
Reading tech blogs regularly will keep you up to date on the most recent vulnerabilities and will help you stay one step ahead of hackers.
Use robots.txt to Keep Certain Things Hidden from Search Engines:
Add a robots.txt folder for the documents, images, and information that you do not want to be indexed by search engines.
Use a Secured FTP Access and Restrict Root Access
SFTP access prevents others from being able to view what you are uploading or downloading to & from the webserver. Restrict the access to certain non-system folders to prevent FTP uploads by people other than the system administrator.
Check Your Software and Third Party Scripts:
Ensure that any software you use is kept up to date with the latest security fixes. (Blogging software like WordPress, third party scripts, etc.) Also remove any scripts, services, or other software that you are no longer using.
Perform Security Testing:
It is important that once you have the previous security items in place that you perform security testing. Search your website and source code for any security flaws that may allow unauthorized access. You can check your source code for free with Source Code Analysis Tools. Using security plugins like WordPress Security Scan are also a great way to analyze the security of your site.
Keeping your website secure is a never ending job, there will always be new threats and hackers will continue to find new ways to gain unauthorized access. Implementing these suggestions in addition to doing your own research will help you to stay as far ahead of these types of individuals as possible
Thanks for Reading!
Dustin
Providing Tech Support for Businesses in Maryland






 Hey, everyone, welcome back to the
Hey, everyone, welcome back to the 

