Author Archive
Thursday, August 25th, 2011
Tuesday August 23, 2011 Facebook made several announcements, the majority of which addressed the upcoming sharing and privacy improvements. In addition Facebook addressed smaller topics like the phasing out of the mobile only “Facebook Places” and the renaming of a long time Facebook attribute.

from http://blog.facebook.com/blog.php?post=10150251867797131, August 2011
Privacy and security have always been a major concern for Facebook users. In response to these worries Facebook has made multiple changes to the process for sharing posts, photos, tags, and other any other content. The new set up focuses on making the policies of concern more assessable and understandable to all users. The following Profile Control changes are expected to begin rolling out sometime this week, at that time users will encounter a prompt to tour the new Facebook Profile Features. (August 25, 2011)
The primary adjustment to the new profile is the new location for the privacy and sharing controls. The sharing controls are now available directly on a user’s profile page. These controls were previously only available on the settings pages. The aim for this redesign is to present users with a clearer and more consistent sharing experience. The new inline drop down menus that are now located next to the content posting area can enable a user to instantly adjust who has permission to view the content. Whether it be your thoughts, images, or videos each user will be able to see who can view their content and allow them to grant or deny access with one simple click. Additionally, since many of the settings options have been compiled into these smaller inline menus the previous settings page has also been simplified.
Also launching with the new profile sharing controls is the following sharing, tagging, and privacy policies.
- Control who can view your post while posting
With the old setup a user would have to access the settings page in order to change any privacy or sharing settings. The new adjustments make it easier for users to assign who can view their content at the time of posting.
- Restrictions Are Not Permanent
Sharing restrictions can be changed at any time for each individual post. After posting something to your co-workers that was supposed to be for your friends you can simply switch the posts authorizations and avoid any misunderstandings.
If you tag yourself on someone else’s pictures the tag will first need to be approved before it appears.
- Tagging People You Don’t Know
You can now tag anyone on Facebook not just people that you are friends with. When a user is tagged on Facebook a permission request form will be sent to that used.
- Tagging Pages You Don’t Like
You can now also tag pages on Facebook that you haven’t liked. Again the page will need to consent to the tag in order for it to appear.
When tagged by another user in their content the tagged person will be presented with an approval request form. This form will provide a user with the options to reject the tag, request that the picture be removed, or even block the user.
Users have requested that they want to see their profile the way that other users view them. In order to see how others view you on Facebook they have added a new “View Profile As” button in the top right corner.
The “Everyone” attribute is now being called “Public” to better describe the behavior of the post
- No More Mobile Only Facebook Places
Users will be able to add locations anywhere (posts, pictures….) and from any device which is why they are deciding to phase out Mobile only Facebook Places.
The recent overhaul is thought to be in response to Google+ which was just launched in July and is already becoming a major competitor. Facebook’s new updated features are an attempt to show their customers that they listen to their requests and always have a strong focus on user privacy and protection.
Check out the Google Blog where Chris Cox the Facebook VP of products, Explains the new features .
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: Facebook, Information Security, post, posting, privacy, social networking
Posted in Social Networking | No Comments »
Friday, August 19th, 2011
Thursday August 18, 2011 Hewlett-Packard confirmed both their recent discussion with Autonomy Corporation regarding a possible offer for the company as well as the upcoming discontinuation of their webOS devices. In a press release HP expressed their plans to discontinue production for webOS devices including the recently released HP Touch Pad. HP also reported that its board of directors had approved the exploration of strategic alternatives and that they will be considering a wide range of options such as full or partial separation of the Personal Systems Group from HP through a spin-off or other transaction.

from http://www.hp.com, August 2011
This decision follows only 2 months after HP latest product launch, the HP Touch Pad. The HP Touch Pad was initially thought to be a major competitor for the iPad. However, following a rocky launch that included an announcement of a better model just days after the initial release, drastic price changes, and bad PR it was clear that HP had fumbled the release and the HP Touch Pad didn’t stand a chance against the iPad or other competitors.
Along with the dwindling release sales for their new tablet HP was also far behind their mobile competitors. Although the fastest growing consumer electronics are mobile devices according to HP’s chief financial officer Cathy Lesjak “the webOS would require significant investments over the next five years, generating a risk without clear rewards”. HP webOS users currently only account for 3% of the market while Android occupies a steady 40% and Apple controlling fewer than 30%.
HP also faced struggles obtaining developers to build applications for their devices. The more developers there are usually means more applications and more importantly more customers. However because the platform with the most developers usually attracts the most customers and the platforms with the most customers usually draw in the most developers it can be very difficult for new devices and platforms to even get off the ground.
HP now seems to be modifying their strategy and shifting from consumer electronics to developing large software for businesses. This new direction is evident with the latest $10 million acquisition for Autonomy. According to Léo Apotheker, HP president and chief executive officer
“Autonomy presents an opportunity to accelerate our strategic vision to decisively and profitably lead a large and growing space,” said. “Autonomy brings to HP higher value business solutions that will help customers manage the explosion of information. Together with Autonomy, we plan to reinvent how both unstructured and structured data is processed, analyzed, optimized, automated and protected. Autonomy has an attractive business model, including a strong cloud based solution set, which is aligned with HP’s efforts to improve our portfolio mix. We believe this bold action will squarely position HP in software and information to create the next-generation Information Platform, and thereby, create significant value for our shareholders.”
What does this mean for Apple and Google? Although this has been major news from HP their decision isn’t likely to impact their competitors because they were not a major threat to begin with.
Along with the HP Touch Pad other discontinued HP devices include HP Palm Pre 2, HP Palm Pre Plus, HP Palm Pixi, HP Veer, and the HP iPAQ Glisten.
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: consumer electronics, device, HP, hp touch pad, mobile device, smartphone, webOS
Posted in Electronics, Hardware Overview, SmartPhone | No Comments »
Friday, August 12th, 2011
A couple weeks ago Google announced a new Page Speed Service which is currently available to only a limited number of webmasters. The new Page Speed service follows many previous speed assessment products that Google has released over the years, releases that include the Page Speed Browser Add-ons and Page Speed Online. These previous releases focused on scoring a websites speed performance and providing users with suggestions or feedback to increase their speed score.

from http://code.google.com/speed/pss/index.html, August 2011
The new Page Speed is a service that doesn’t analyze your website’s speed but instead automatically increases it. The new service retrieves your content from the website server, rewrites the website using their specified guidelines, and then delivers it the site visitor even faster using their servers.
While using the Page Speed Service a website can expect to see a 25%-60% improvement however the exact amount of speed depends on a number of different factors. These factors include the amount of content on your pages, the browser, geographical location, bandwidth and more. Visit the web page test to analyze your website and determine the exact speed increase that the new page speed service can produce for your website.
The test works by simply visiting your site and then repeating the same test by substituting your website into the Page Speed Service. The test takes only minutes to perform and once complete the user is presented with a chart that details the load time from the original server, the load time from the Page Speed Service, the load time for repeat visits from both servers, the percentage of the speed increase, and multiple links to test details. The results also provide a visual rendering for the two speeds that clearly demonstrate to the user the exact amount of speed that they can expect to gain by using the Google Page Speed Service.
Visit the link to request to participate in the new Page Speed Trial.
How to use the Service:
- Log into the Google APIs Console.
- Provide the serving domain of the website you want to speed up.
- Verify ownership of the domain through Google Webmaster Central.
- At this stage, you will have an opportunity to preview how your site will look when rendered through the Page Speed Service.
- Set up and provide the reference domain from where Page Speed Service will fetch your website content.
- Change your site’s DNS CNAME entry and start using Page Speed Service to serve traffic to your users.
- Monitor traffic and latency metrics for your web site from the Dashboard
Currently Google is offering this service free of charge to a limited number of users. At the conclusion of the trial period later this year the product will be available to everyone at a competitive price.
When performing a web page test for our own website we were able to see a 29% increase in our speed. For the best results we recommend using a combination of Google Page Speed online to determine how to reduce your website’s load time and the Page Speed Service to get an extra speed boost.
For more information visit the Page Speed Service FAQ.
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: google, Google Page Speed, load time, page speed, page speed service, service, speed, speed boost
Posted in Google, Web Development, Web Tips | No Comments »
Friday, August 5th, 2011
According to a recent Tweet from Matt Cutts, Google has released their biggest spam report form refresh in roughly ten years. Along with their own attempts Google also relies on individual users to help combat websites that are spamming their index. As a part of Google’s continuous effort to improve the quality of search results, they ask that you submit a spam report if you come across a site that isn’t following the webmaster guidelines or acceptable practices. Google users can submit spam reports using their Webmaster Tools. 
The previous spam report form was only a single page and had simple check boxes for users to identify the type of spam that was encountered. The new spam center however has a main page that provides a user with 8 different links. Each of the 8 links is for a different type of spam. The links include paid links, objectionable content, malware, other Google products, copyright, legal issues, personal/private, phishing, and other. These links will each direct a user to a separate spam complaint section where the user can then report the web address and express their concerns in full details.
Google depends on their “webmaster quality guidelines” as well as these detailed spam reports to help them generate scalable spam solutions. Instead of struggling against spam one by one they are always seeking new information to enhance their algorithm and combat large bodies of spam. Google’s quality guidelines express the various forms of deceptive or manipulative behaviors and describe how websites can avoid the misleading practices. The basic quality guidelines established by Google are as follows:
- Design pages for users, not for the search engines. Don’t deceive your users or present different content to search engines than you display to users (cloaking).
- Don’t use tricks that are intended to improve search engine rankings. A good rule of thumb is whether you’d feel comfortable explaining what you’ve done to a website that competes with you. Another useful test is to ask, “Does this help my users? Would I do this if search engines didn’t exist?”
- Don’t participate in link schemes designed to increase your site’s ranking or PageRank. In particular, avoid links to web spammers or “bad neighborhoods” on the web, as your own ranking may be affected adversely by those links.
- Don’t use unauthorized computer programs to submit pages, check rankings, etc. Such programs consume computing resources and violate our Terms of Service. Google does not recommend the use of products that send automatic or programmatic queries to Google.
- Don’t create multiple pages, subdomains, or domains with substantially duplicate content.
- Don’t create pages with malicious behavior, such as phishing or installing viruses, trojans, or other badware.
- If your site participates in an affiliate program, make sure that your site adds value. Provide unique and relevant content that gives users a reason to visit your site first.
These are only the basic quality guidelines. In order to prevent your site from being flagged by Google it’s advised that you follow the mentioned suggestions as well as the rest of the Webmaster Guidelines. If your website does fail to comply with Google’s requests then you should make the necessary adjustments and resubmit your website.
To compare the new and old spam report forms visit SearchEngineLand.com
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: google, google spam report, spam, spam report, webmaster guidelines, webmaster tools
Posted in Google | No Comments »
Friday, July 29th, 2011
Earlier this month the WordPress version 3.2 update was released. Version 3.2 is the first WordPress update that requires PHP 5.2.4 or greater and MySQL version 5.0 or greater. WordPress made the announcement concerning the discontinued use of PHP 4 and MySQL 4 a year prior its release to give users ample time to prepare for these changes. WordPress provides several resources for upgrading WordPress but despite the extra preparation many users have encountered bugs in the recent software. Since the release most of the issues have been resolved with the 3.2.1 update however some users continue to experience problems.
Before we began upgrading our own WordPress we first made certain that we met the required specifications. After completing the version 3.2 update we began to experience some problems on our Internet Beacon blog. The issue we encountered didn’t impact our blog but rather our recent blog PHP script that is located on the bottom of our Internet Beacon home page. This section would normally list some of our latest blog but following the update it stopped generating content.
from http://www.internetbeacon.com/, July 2011
Unaware of how to rectify this issue we consulted with the WordPress community and various chat boards. This matter also spurred us to write the blog WordPress 3.2 is Available: Are you ready for the Upgrade? In this blog we informed readers of the buggy nature of 3.2 and detailed how to be prepared for the upgrade as well as how to make certain you can reverse the upgrade process. During the weeks following this post we were still unable to resolve our problem. We did however recently determine how to reverse the upgrade which eventually fixed our issue.
Like most updates there is always a chance that errors can occur which is why it is recommended to perform a backup prior to the process. Are you still experiencing problems? One possible option is to downgrade to your previous version, assuming that you made a backup before updating. This will reverse any changes performed on your WordPress and more than likely fix your problems. If you are experiencing an issue with the new version of WordPress and you have a backup of your previous version the following steps will walk you through the WordPress downgrade process.
(Note this is just a suggestion from our personal experience and the downgrade process will only fix the issues caused by the update, we also do not claim that downgrading WordPress will solve every issue)
- Backup your root WordPress folder and move a copy to a local computer
- /public_html/blog-07-27-2011. Zip
- Download your preferred old version of WordPress from WordPress Release History Page.
- Unzip and extract the File (Remember where you save the extracted file.)
- You can use FileZilla, the free FTP solution
- Open Filezilla, go to public_html, delete the wp-admin and wp-includes
- In Filezilla local site, look for the WordPress file that you downloaded in step 1
- Right-click wp-admin and upload.
- Go to login
- Upgrade database
- Close all tabs and open your own http://yourwebsite.com/wp-admin (replace yourwebsite.com with your own website name)
This method worked for our website, hopefully it can help you!
In most cases it’s always recommended that you update your software as soon as updates become available. This ensures that you have the latest security and support for the software. However after this situation it might be worthwhile to wait a short amount of time before updating to allow developers to work out the kinks. A key lesson learned from this situation is the importance of making a backup prior to making any major change. If you still experience problems the WordPress community forums are a great place to start and contain a ton of helpful information, if you don’t know how to fix something yourself it never hurts to ask.
Read Our Original Post
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: backup, downgrade, restore, Update, wordpress, wordpress 3.2, wordpress downgrade
Posted in Software | No Comments »
Thursday, July 21st, 2011
On Wednesday July 20, 2011 the Obama Administration announced their plan to close 800 of their 2,000 data centers over the next four years. The Federal Government initially scheduled the shutdown of 137 data centers by the end of this year. However, currently the process is ahead of schedule with already 81 sites closed so they now expect the closure of 195 facilities. In addition to the revised figure of 195 data centers for 2011 the White House also announced that nearly 200 complexes will be closed by the end of 2012, making the accumulative shutdowns just shy of 400 data centers.
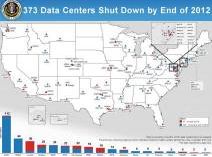
from http://www.whitehouse.gov/blog/2011/07/20/shutting-down-duplicative-data-centers, July 2011
Since 1998 the United States Government has quadrupled their amount of data centers. Throughout the years the development of software that allows for multiple platform access has enabled the government to become more efficient and reduce their need for most data centers. It is reported that many of these sites operate only using 27% of their computing power even though taxpayers continue to pay for the entire infrastructure (land, facilities, equipment, cooling processes and special security elements).
According to the plans of the United States Government, the elimination of these data centers will help them be more efficient during this time of deficit. Over the next four years the shutdowns will allow for more real estate and a drastic reduction in unnecessary spending. The data centers that are marked for termination range in size with some occupying over 200,000 square feet and others residing on only 1,000 square feet of land. The geographic locations of these data centers also vary with locations scattered throughout 30 states. Due to the special equipment contained within these data centers the average power consumption can be 200 times more than regular office buildings and is enough to power 200 residential homes.
As a component of the President’s Campaign to Cut Waste, the closures will assist in locating misused tax dollars. The 800 sites scheduled for elimination further build on the Administration’s ongoing effort to create a more efficient, effective and accountable Government. According to Jeffrey Zients the Federal Chief Performance Officer and Deputy Director of the U.S. Office of Management and Budget“By shrinking our data center footprint we will save taxpayer dollars, cutting costs for infrastructure, real estate and energy. At the same time, moving to a more nimble 21st century model will strengthen our security and the ability to deliver services for less.”
This data center efficiency plan is aimed to save taxpayers over 3 billion dollars and greatly decrease environmental impact. Along with the plan to close these data centers the Government’s goal is to go in the direction of cloud services, first focusing on email and storage. The transition to cloud based computing provides a tremendous savings opportunity. According to an interview with Vivek Kundra, chief information officer for the federal government, tapping into cloud computing services could save an additional five billion per year. She also expressed that as the services continue to grow they will continue to transfer their efforts from redundant systems to improving the citizen experience.
Absent from the announcement was the mention of job impact. Although data centers do not typically employ a tremendous amount of manpower, analysts still believe that tens of thousands of jobs could be displaced or impacted by future shutdowns.
What do you think? Are the closures a good opportunity to reduce the Government’s wasteful spending and taxpayers to save money or is the possible effect on IT professionals too much?
For more information visit The White House’s Blog.
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: Campaign to cut waste, cloud, data, data center, government, shutdown, storage
Posted in Server, Storage | No Comments »
Wednesday, July 13th, 2011
Scams, viruses, and Facebook Frauds that prey on the curiosity of unsuspecting users are nothing new for the popular social network. Facebook and social networking sites alike create a perfect environment for spammers to instantly reach millions and rapidly spread their lucrative scams. Although the majority of users have learned how to Spot and Avoid Facebook Scams, there are some creative and devious scams that continue to attract the attention of many users. These scams are extremely misleading and publicize something that is either too good to be true or reel users in by taking advantage of the recent headlines.

from http://www.facebook.com/group.php?gid=9874388706&v=wall, July 2011
These scams are usually created to generate some kind of financial gain for spammers and to further spread their spam. Often the fraudulent posting will advertise one thing and then direct a user to a completely unrelated page. Previous Facebook scam such as the “Free iPad scam” and the “See who is viewing your profile scam” have been used as a spamming technique called ClickJacking.
ClickJacking presents a page to the user with a seemingly harmless action button, unbeknownst to the user there is usually a transparent layer with an alternative button positioned directly on top. In other words, when the user thinks that they are clicking the one button they are really clicking the hidden button. The hidden button is usually something that a user would probably avoid if given prior knowledge. For example the button could initiate an unauthorized purchase, an adjustment to your social profile, a twitter follow, or the spamming of your Facebook contacts.
New spam scams are created each day, this week alone we have already seen three new Facebook scams that draw in users by exploiting popular news headlines. Among the scams that appeared this week are posts proclaiming the “Death of Charlie Sheen”, the “Casey Anthony murder confession video”, and the “Google+ invite”. Each of these attractive headlines is completely bogus and only serves the purpose of luring in victims.
The high demand for Google+ invites has made eager users a perfect target for spammers. For this scam a user receives a request to access their basic information. Once the user accepts that request the scam bombards them with emails, submits posts on your friends’ walls, and accesses their personal information while they are offline. In addition to these abrasive actions the scam is also thought to be accumulating email accounts for future spam attacks.
The second scam is one that involves the court case of Casey Anthony, who was exonerated and found not guilty of the murder of her daughter due to lack of evidence. The hype surrounding the court case and public outrage regarding the jury’s verdict has generated a lot of attention for Casey Anthony. In this scam a user receives a message offering a chance to watch the video of Casey Anthony confessing to murder. Upon clicking, users are redirected to a site that presents them with a survey that must be completed before watching the video. Following the completion of the survey the users do not gain access to a video but instead encounters more surveys. Similar to the first scam, both the walls of the users as well as their friend’s walls are blasted with Casey Anthony Spam postings.
Like the previous scams the “Charlie Sheen Found Dead Scam” also capitalizes on the public interest for Charlie Sheen ever since his termination from “Two and a Half Men” and whacky behavior. This scam again obtains user information and redirects them either to a dead page or one that requires them to participate in an online survey.
Again these claims are completely bogus and are only used so that spammers can benefit from susceptible users. If you have had the misfortune of coming across these scams or ones like them, perform the following tips to cleanse and secure your Facebook profile.
If something sounds too good to be true or is too shocking, then it’s probably a scam. When it comes to social networking sites, try stay up to date with the latest scams and be cautious and suspicious of all content that appears shady.
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: casey anthony scam, charlie sheen scam, Facebook, google+ scam, scam, social network, spam, spammer, spamming
Posted in Information Security, Social Networking | 1 Comment »
Friday, July 8th, 2011
According to the Recording Industry Association of America (RIAA) several industry leaders from music, movie, television and broadband services have teamed up to educate consumers and diminish online content theft. Among the organizations volunteering are Walt Disney Studios Motion Pictures, Paramount Pictures Corporation, Sony Pictures Entertainment, Twentieth Century Fox Film Corporation, Warner Bros. Entertainment Inc, Universal Music Group Recordings, Warner Music Group, Sony Music Entertainment, EMI Music North America, AT&T, Comcast Corp, and Verizon. These companies and more have all come together to create the foundation for the new Copyright Alert System.
from http://www.riaa.com/toolsforparents.php?content_selector=legal-music-services July 2011
Piracy is a major problem and even with the increased prevention and restrictions it continues to plague the various entertainment industries. For most individuals downloading protected media is often viewed as a minor crime, if one at all. When compared to other illegal activities it does seem minor however when considering the worldwide accumulation of pirated material obtained without compensation the loss and industry devastation is in the millions. The impact of piracy is felt by all parties involved in the media creation process and not only does it affect jobs but the future production of the content we enjoy. As the volume of pirated content continues to increase the amount of revenue continues to decrease and even with digital sales the earned revenue isn’t enough to make up the loss.
P2P file sharing programs like LimeWire are illegal as you can tell upon visiting their court ordered deactivated website. Organizations like the RIAA continually monitor these applications and focus their resources on disbanding them. Fortunately for users there is a ton of legal alternatives for low cost digital content. Some of these programs include Amazon, iTunes, Napster, Pandora, and AOL Music.
According to the RIAA Piracy FAQ
- In the decade since Peer-to-Peer sharing sites like Napster emerged in 1999, the music sales in the U.S. have dropped 47 percent. ($14.6 billion to $7.7 billion)
- From 2004 through 2009 approximately 30 billion songs were illegally downloaded.
- Only 37 percent of music acquired by U.S. consumers in 2009 was paid for.
- United States Internet users annually consume between $7 and $20 billion worth of digitally pirated recorded music.
- Digital theft of music, movies and copyrighted content takes up huge amounts of Internet bandwidth (24 percent globally and 17.5 percent in the United States)
- While the music business has increased its digital revenues by 1,000 percent from 2004 to 2010, digital music theft has caused the global market decline of around 31 percent in the same period.
- Global music piracy causes $12.5 billion of economic losses every year
- Piracy has resulted in the loss of 71,060 U.S. jobs, the loss of $2.7 billion in workers’ earnings, the loss of $422 million in tax revenues, the loss of $291 million in personal income tax, and the loss of $131 million in lost corporate income and production taxes.
The new copyright alert system is said to work similar to a fraud alert warning. This new system will alert users when their Internet service account may have been used to obtain the stolen content. When a user is suspected of content theft the Copyright Alert system will initiate an email or pop-up window warning. A user will be given up to 6 of these warnings before the Internet service provider begins to take mitigations measures. In order to inhibit users from repeated content theft ISP’s can potentially take actions that include slowing the web speed or redirecting the user to a page with “please contact your Internet Service Provider”. However, the telecom companies will not turn over the names of the individuals who pirated the content nor will they shut down the Internet service for that user.
Prior to this cooperation Internet Service Providers didn’t have a solid framework to operate on when faced with copyright theft. They would often simply forward the notification or complaints from the content owner to the user suspected of pirating content. The parties involved with this new agreement aim to create substantial guidelines and best practices that sufficiently alert subscribers, protect copyrighted content and influence the use of legal online content.
The six warning early notification system was established because in some cases the users might not know that the content is illegal or even being accessed. For example parents may not realize that their children are downloading content. The early warning system will provide sufficient warnings so that the parents or users who may be intentionally obtained illegal content can rectify the situation, prevent future incidents and avoid the ISP’s mitigation methods.
The RIAA expresses that “The Copyright Alert System is based on a consumer’s “right to know” when his or her Internet account may have been used improperly to download copyrighted content. The data suggest that, once informed about the alleged content theft and its possible consequences, most Internet subscribers will quickly take steps to ensure that the theft doesn’t happen again.”
The partnership has also called for the creation of a Center for Copyright Information to offer support and education for consumers. The Center for Copyright Information as well as the Copyright Alert System and ISPs will begin incorporating Copyright Alerts in 2011 and 2012. Through education and implementation, this alliance sets forth to not only eliminate piracy but influence future collaborations to achieve common goals.
For a full list of companies involved in the Copyright Alert System Framework visit RIAA Company Collaboration.
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: content, copyright, copyright alert system, digital download, digital media, Legal, media industry, piracy
Posted in Legal, Piracy, Software | No Comments »
Friday, July 1st, 2011
It was only a year ago that Google implemented a new visual design that focused on providing users with a visual refresh and a convenient sidebar navigation tool. The June 2010 updates also introduced a time based search feature that enables users to search during a period of time such as the last 24 hours, the past year, or a custom range. During Google’s Spring Metamorphosis last year they had mentioned that they are always working on improving the design and experience of Google which has led to many of their latest changes. Users may have noticed that on Tuesday June 28, 2011 that some changes had taken place in an effort to evolve the design and Experience of Google. Not only did Google modify its search engine but that same day Google had also announced the Google+ Project.
from http://www.google.com July 2011
The clean, spacious, and simple design of Google+ coordinate with the new look of Google and are already carrying over to the other Google services like Gmail. The new Google home page has even gone through its own changes. Now with a smaller logo and the links moved to the top and bottom edges, the page has a cleaner and more intuitive feel. Additionally Google now has a universal toolbar that is located at the top of the page and is also consistent across each page and service.
According to Google, “The way people use and experience the web is evolving, and our goal is to give you a seamless and consistent online experience—one that works no matter which Google product you’re using or what device you’re using it on”
In their Google Blog, Google mentions that their new design was based on 3 principles focus, elasticity, and effortlessness. The new look however is only the first of many changes said to be coming in the following months. When it comes to increasing focus Google plans is to eliminate clutter, use bolder colors, make the buttons more identifiable, and a new “hide” feature that will let the user clear away any unnecessary distractions like navigation buttons. Behind the simplistic design, Google will continue to use the latest technology to provide users with a powerful experience. In addition Google will also be working hard to improve their flexibility across all devices. Their goal is to provide a solid visual experience on every device without losing any elegance and practicality.
Google is always changing in order to enhance and improve the Google user experience. These are only a few of the many changes we can expect to see over the next couple of months, keep an eye out.
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: design, google, Google experience, Search Engine, usability, user experience
Posted in Google, Search Engines | No Comments »
Tuesday, June 21st, 2011
Earlier this month Apple held its annual Worldwide Developers Conference, during the event Apple unveiled the new features of iOS 5 which is set to arrive later this fall . Although the much anticipated release of the iPad2 had come and gone back in March, the news of the newest iOS has seemed to spur iPad2 sales. At a price range set from $499-$829, these devices are definitely an investment that is worth protecting. The following are ten tips to help ensure the safety and protection of iPad devices. The list covers both physical and virtual security so that customers can hopefully prolong the life of their device and be able to take full advantage of the upcoming iOS improvements.
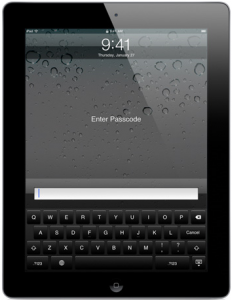
from http://www.apple.com/ipad/features/, June 2011
The iPad Smart Cover isn’t a customer’s only choice however it seems to offer the most protection along with usability. In addition to providing protection, the Smart Cover can also be transformed into an iPad stand with various positions, activate the sleep mode when covered, wake the device when uncovered, grip the iPad using built in magnets, comes in a number of colors and is available in two different materials. Users can also choose to use full shell cases for heavy duty protection or portfolio and envelope cases for the professional environment.
A case or cover doesn’t necessarily mean the screen is fully protected. Screen or scratch protectors are well worth the purchase and not only do they prevent scratches but they have also been known to prevent the screen from shattering on impact. Prior to the release of the iPad2, Apple had stopped selling all anti-glare and screen protection film as what was thought to be a way to advertise the iPads screen durability. However screen protectors are still available through other companies, the trick is finding one that provides durability and is easily adhered to the iPad without causing damage.
It may seem like common sense but some people still leave their iPad unattended or believe it to be safe in their car. A car is not a safe place to leave expensive devices, leaving your device in sight and unattended will only entice someone to break in and steal it. In addition to passwords, iPad owners can also use security locks and security cables to provide extra protection when not in their possession.
At the very least all users should utilize the password option to protect their information and data. To configure the password settings go to Settings, General, and Passcode Lock. Once the password option is activated the passcode will be required when restarting the device, waking the device, and unlocking the screen. Users can also specify how many times the screen must be locked before activating the password prompt. A typical passcode has four digits however they can be changed to a longer alphanumeric code by disabling the simple passcode option.
- Auto-Lock, iPad tracking and other Security Preferences:
The iPad2 comes with a find my iPad app that lets the user locate a stolen or lost iPad as long as it’s still operational. Users can also determine how many password attempts are acceptable before disabling the device or remotely erasing the data from the device. Try to avoid using the common passcodes like 1234 or 0000. The auto – lock will activate the lock automatically after the iPad is inactive for the amount of time specified by the user. If someone does happen to acquire your device then these appropriate security settings along with an adequate password will at least protect your information.
When surfing the Internet from your mobile device there are several options that provide extra protection. For example turning off the Auto-Fill option in the Safari Browser settings will disable the iPad from remember passwords or other critical information. You should also check to make sure that your pop-up blocker is turned on as well as the fraud warning feature. When it comes to accessing websites and email attachments be sure to practice good judgment. Users can also clear browsing history, cookies, and cache so that no information is stored.
It is extremely important that you perform all available updates not only for the iOS but for your iPad applications as well. Updates are often released to resolve vulnerabilities and to protect users against newly discovered malware like viruses and spyware. Updates for Apps can be performed by accessing the app store and selecting update all under the update menu.
- Backup Information on iTunes:
Performing routine backups in iTunes can help protect your information and prevent data loss. In the event that your data or device is lost, corrupted, or stolen, users will still have access to it on their PC’s. The upcoming iCloud can also be used to store backup information.
- Disable Bluetooth when not in use:
While not using Bluetooth it is recommended that you turn off the feature. Allowing Bluetooth channel to remain open can potentially create a vulnerability that is susceptible to intrusion.
- Extra Apps For Extra Security:
Consider purchasing apps that provide enhanced security. Here’s a list of 50 Security Apps that perform functions like storing passwords, activating alarms, monitoring business transactions, and safe web browsing.
Hope these tips help keep your device safe and your information protected. For more details check out Apple.com and keep an eye out for Apple iOS 5 this fall!
These security tips are not limited to only the iPad2, many of them can also be applied to the iPad, iPhone and iPod touch devices.
Thanks for Reading and Have a Great Day!
Dustin
ComputerFitness.com
Providing Tech Support for Businesses in Maryland

Tags: Apple, device, Information Security, Ipad, iPad security, iPad2, password, protect, protection
Posted in Information Security, Mac, iPad | 1 Comment »
|















